-
What is Information Availability (IAV) | IGI Global
The ability to make information and related physical and logical RESOURCES ACCESSIBLE AS NEEDED, WHEN they are needed, and WHERE they are needed. Learn more in: Information Availability
-
Information Availability: Security & Forensics Book Chapter | IGI Global #ril
-
This chapter describes the concept of information availability (IAV) which is considered an important element of INFORMATION SECURITY. IAV is defined as the ability to make information and related resources accessible as needed, when they are needed, where they are needed.
In the view of the authors, this notion encompasses more than just making sure that the information technology (IT) INFRASTRUCTURE is technically adequate and continuously available, but it also emphasizes other often-ignored attributes of IAV, such as APPROPRIATE POLICIES AND PROCEDURES, an effective security policy, and the establishment of a workable BUSINESS CONTINUITY PLAN. Thus, the goal of the chapter is to define IAV in the context of information security and elaborate on each of these first and second order determinants of information availability.
-
-
What is information availability and information unavailability? Explain BC planning life cycle (2017-12-02) #ril
-
Information availability (IA) refers to the ability of the infrastructure to function according to BUSINESS EXPECTATIONS during its specified time of operation.
Information availability ensures that people (employees, customers, suppliers, and partners) can access information WHENEVER THEY NEED IT.
-
Information availability can be defined with the help of reliability, accessibility and timeliness
Reliability: This reflects a component’s ability to function without failure, under stated conditions, for a specified amount of time.
Accessibility: This is the state within which the required information is accessible AT THE RIGHT PLACE, TO THE RIGHT USER.
Timeliness: Defines the exact moment or the time window (a particular time of the day, week, month, and/or year as specified) during which information must be accessible. For example, if online access to an application is required between 8:00 am and 10:00 pm each day, any disruptions to data availability outside of this time slot are not considered to affect timeliness.
-
-
做資安往哪走:企業資安的定義與目的 - iT 邦幫忙::一起幫忙解決難題,拯救 IT 人的一天 (2020-09-18)
-
下列三點稱為C.I.A.資安核心三要素:
- 機密性(Confidentiality):指訊息不為其他不應獲得者獲得,保障訊息在對的人、對的時間、對的裝置和對的地點上被存取,用以維護用戶資訊的保密性,
- 完整性(Integrity):指在傳輸、儲存資訊或資料的過程中,資訊或資料不被未授權的篡改。
- 可用性(Availability):簡單的說,可用性就是讓一個系統處隨時可工作狀態,資訊服務不因任何因素而中斷/停止
-
另外除了三要素外,另還可加上身分驗證 (authentication)、存取控制 (Access Control)、不可否認性 (non-repudiation)三項組成共同組成更妥當的資安基本原則:
- 身分驗證-Authentication:確保使用者登入時該數位身分有合理妥當的檢驗。
- 存取控制-Access Control:確保任何操作或人員均有適當的權限界定且受到合規的授權。
- 不可否認性-Non-repudiation:確保無法否認於系統上完成的操作,例如數位簽章是讓寄件人無法否認這封信就是從這發出來的。
-
企業資安主要圍繞著"穩健營運"、"永續經營"和"風險控制"等的商業活動確保為主軸,對於網路上的種種資訊戰,不用奢望打贏人家,只求安穩度過每一日,即達成資安的基礎目的,很簡單吧。合理的安全管理可以將公司組織的風險降低到一個可以接受的程度,並且持續維持下去。
小提醒:除非不要用,不然風險是無法零化的,只有降低降低再降低。
常見資安框架
-
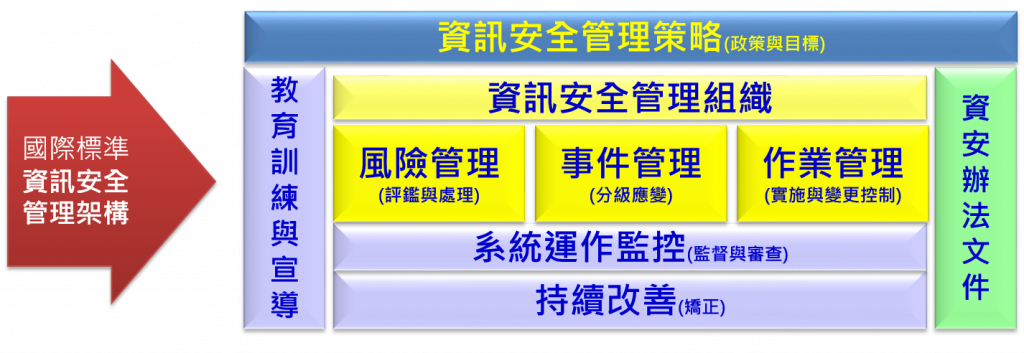
ISMS: 資訊安全管理系統(Information Security Management System, 簡稱ISMS),為一套有系統地分析和管理資訊安全風險的方法。
-
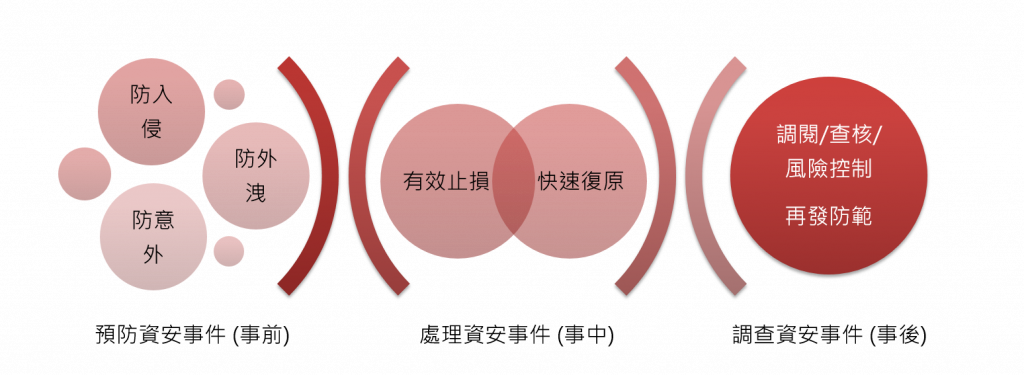
ISO27001: 承襲自ISMS,於2005年被國際標準組織(ISO)採納為ISO 27001。ISO 27001 是一套完整的國際標準,協助企業持續進化,全面性架構起企業組織的資訊安全管理系統機密性、完整性及可用性,從事前預防、事中監控、事後應變等不同面向的管理規劃,協助企業在持續強化資訊安全管理時,也得以掌握風險管理的有效性。
ISO 27001可說是最廣為接受且受到尊崇的普遍性資訊安全管理標準,從初代的ISO27001:2005到當今的ISO27001:2013,持續因應資安發展而演進中。
-
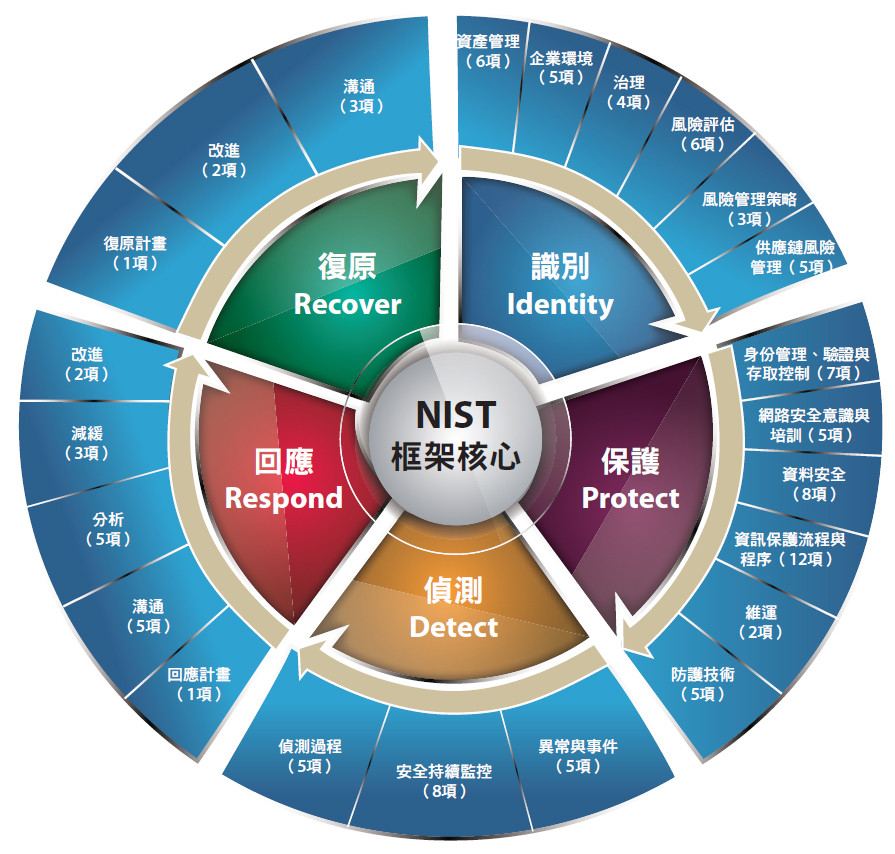
NIST CSF :美國國家標準與技術研究所(NIST)提出的網路安全框架,Cybersecurity Framework(CSF),涵蓋了資安的5大面向,包括識別、保護、偵測、回應與復原,對於企業而言,可供建立網路安全生命週期的風險管理。
-
資安實務是一種取捨分析(TOA),資安做的越嚴謹大家越不方便且影響企業流程甚鉅;反之越鬆散則越不安全、危險但大家都很方便開心。因此,合理的資安政策要適時的、因地制宜的做取捨分析(Trade-off Analysis),或是安排配套措施,取其兼顧營運和風險的平衡點。
-
-
Availability in Information Security - GeeksforGeeks (2020-01-24) #ril
- Availability is one of the three basic functions of security management that are present in all systems. Availability is the assertion that a computer system is available or accessible by an authorized user whenever it is needed. Systems have high order of availability to ensures that the system operates as expected when needed. Availability provides building of fault tolerance system in the products. It also ensures the backup processing by including hot and cold sites in the disaster recovery planning.